
Professional advice makes the difference
Do the right thing
There is no question that companies need to protect themselves against cyber attacks. But which measure and which methods are appropriate? Do you know your security status in order to plan the next steps? Where do you need support? Our security consultants take a close look at your situation.
At the end, there is a concrete to-do list that makes your company more resilient, step by step.
Vulnerability increases
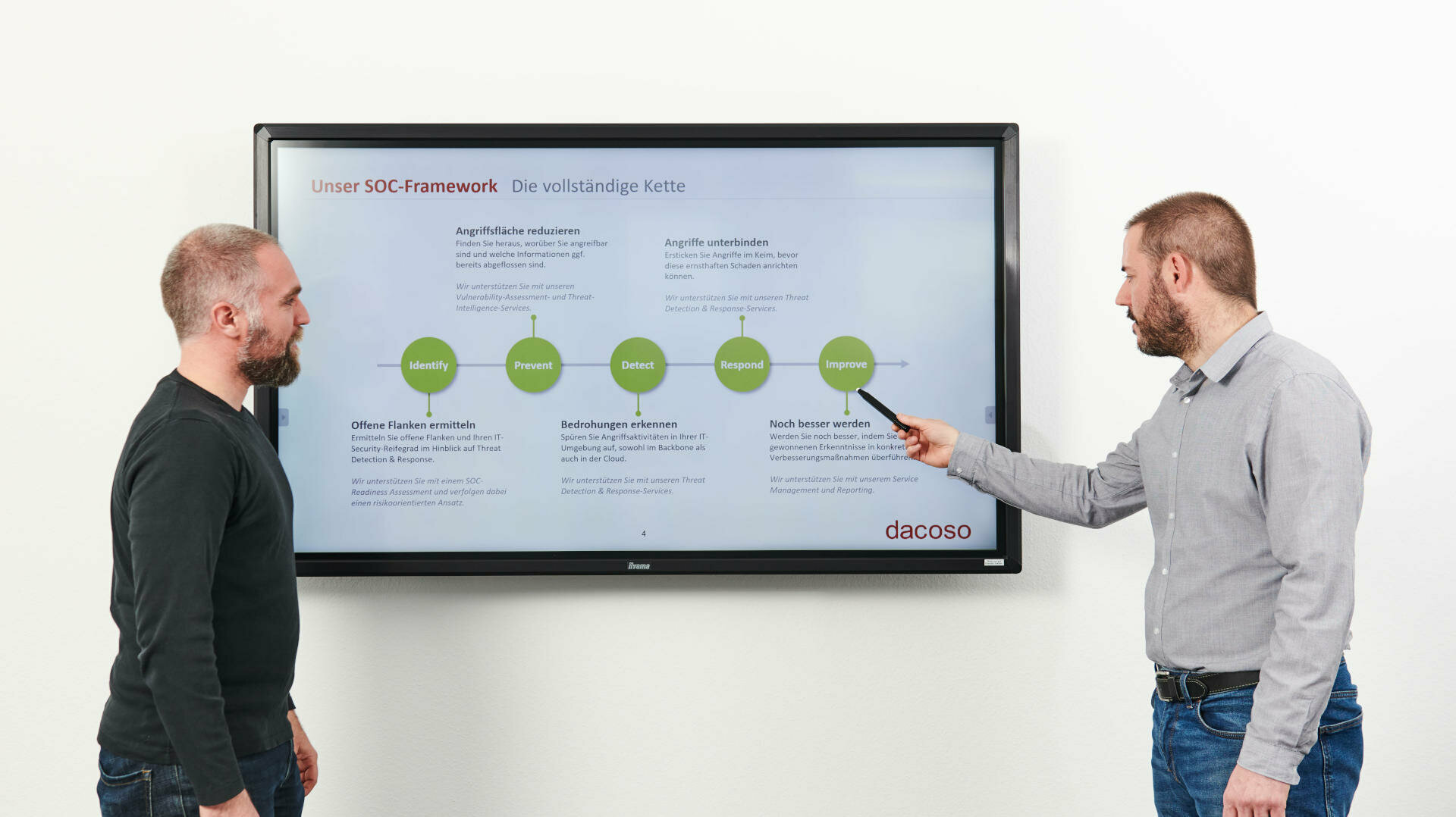
Digitisation is the unstoppable engine of the economy - but it also has its price: companies have become more vulnerable. Hackers act extremely professionally, cyber attacks are becoming more and more sophisticated. And with each new topic, such as cloud, IoT or Industry 4.0, new attack surfaces open up. Firewalls and virus protection - the classic security solutions - have long since reached their limits.
Just no actionism
Security products are springing up like mushrooms and promise fast and comprehensive protection. But you can't do everything at once anyway - take your time and start with an assessment: How well is your company currently positioned in terms of cyber security? And does your team know where the most dangerous gaps are? What is the best way to manage the many risks in your specific situation? Where should your priorities lie? This is where we tip in our expertise: The dacoso security consultants go into conversation with you to work out the biggest pain points in your security status. We do this by listening and asking questions - and by using methods that enable us to validly prove the gaps and propose concrete solutions for them.
Threat intelligence: Detect threats on the Darknet
What information about your company is available to potential attackers on the Darknet? What real dangers for data theft and data sabotage do you have to assume? We find this out for you with our Threat Intelligence solution by uncovering outgoing data on the internet (clear, deep and dark web) for you - with a combination of automated methods (software) and analysis by our cyber security experts. From the results, we develop strategies on how you can reduce the attack surface.
Vulnerability assessment: Identify weak points
Within the framework of an automated vulnerability assessment, we can find and quantify security gaps in your IT systems and networks. How great the risks actually are is assessed by our consultants. At the end, you receive a meaningful report on your vulnerabilities, which serves as the basis for improvement measures.
Penetration testing: Where do hackers find loopholes?
Penetration testing is also shortened to pentesting or pentest. This refers to the simulated security check of selected systems, networks and applications using the methods of a criminal attacker.
In a fake attack, our pentesters slip into the role of the attackers and look for common and unusual vulnerabilities that can be exploited. Of course, the attacks are not carried out and your business operations are not endangered. But every potential loophole is documented and evaluated. Afterwards, you will receive concrete suggestions on how to prevent the attacks - and how you should prioritise the elimination of the vulnerabilities in order to effectively strengthen your IT security.
Red teaming: We set fires deliberately - can you put them out?
While the pentest aims to uncover as many entry points in your company as possible, red teaming involves setting fire to a specific spot: In a targeted attack against your company network, we simulate an Advanced Persistent Threat and have nothing more than your company name available for this. In this way, we check whether and to what extent your IT security measures are effective - or how long it would take an attacker to hijack your IT in different ways.
If necessary, red teaming missions also put the sensitivity and know-how of your staff under the microscope - by simulating a phishing attack or also by means of a physical assessment: Can we physically enter your company premises by exploiting gaps in access control, in processes and in the awareness of employees? At the end, it becomes very clear where there is a concrete need for action.
The results
And now?
We do not leave you alone with the results of the security checks. Our experts analyse your security situation together with you and, if necessary, develop a customised roadmap for more cyber security in your company. In doing so, we keep an eye on which solutions are already being used in your company, how they can be optimised and supported by further measures and services. Our Security Operations Centre (SOC) is available as a platform for the integration and monitoring of all security solutions.