Security Operations Center (SOC) as a Service
Customised safety
You don't always have to go all out - take what you really need: With our SOC as a Service, we offer you the chance to protect yourself against attacks on your data in a highly professional manner. In the style of a large corporation, but without having to invest in infrastructure and personnel yourself. And above all: You remain free in your decisions and use exactly the Managed Security Services that fit your situation - in your customised Security Operations Centre.
Managed security services
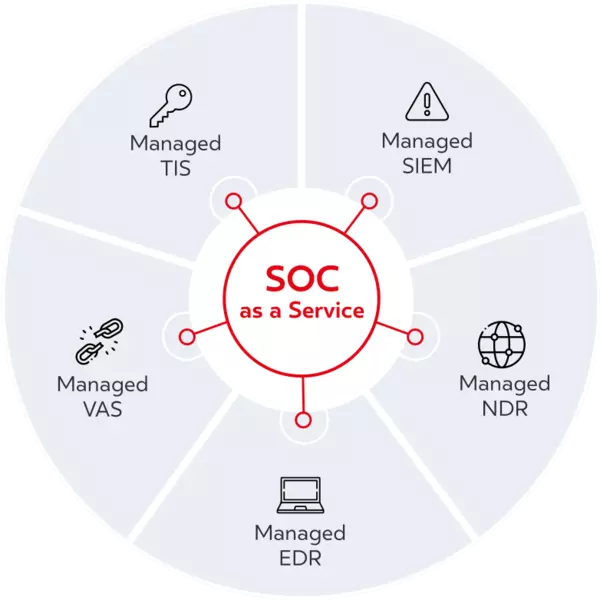
Through our SOC platform, we operate various managed security services that effectively protect your data through automation and artificial intelligence. You choose according to your requirements. All modules together form a comprehensive protection of your company against attacks. And of course we take care of the interaction with the security solutions that are already being used in your company.
Reduce the attack surface with managed services
Become active where there is still work to be done in your company and get our modular support for this: We have developed services for all levels that implement your individual security goals. The measures are managed and controlled with 24/7 monitoring via the SOC. You also have the option of integrating your existing security solutions here. In the event of anomalies, our experts will alert you immediately and clarify with you whether and how you need to react.
Our Managed Security Services are based on a methodically mature security model (dacoso Cyber Security Framework), which is based on internationally recognised standards such as NIST and CIS. It serves as a framework for action to deal with the adversary in different forms and at different levels - from risk analysis to better precautions to targeted countermeasures in the event of an attack.
Keeping an eye on your security solutions 24/7
With SOC as a Service, you ensure the best possible cyber security without straining your own resources: Instead of setting up and permanently operating your own Security Operations Centre, you can make use of the expertise and experience of our security professionals on an ad hoc basis. Security specialists trained in Germany, who are constantly undergoing further training, monitor your security solutions in the SOC - on request around the clock and always in close contact with you. Our team is trained to quickly uncover new, unknown attack methods and to develop effective countermeasures. In this way, we help you identify threatening security gaps and eliminate the security risks for your company as quickly as possible.
The human factor
Assessing your security situation correctly and acting wisely - without people, the best technology does not work. We invest heavily in our security experts, who are highly trained and undergo continuous training. They have an overview of the latest cyber risks and the right measures against them. From the vast amounts of security data generated for you in the SOC, they draw the relevant information and derive concrete actions from it.
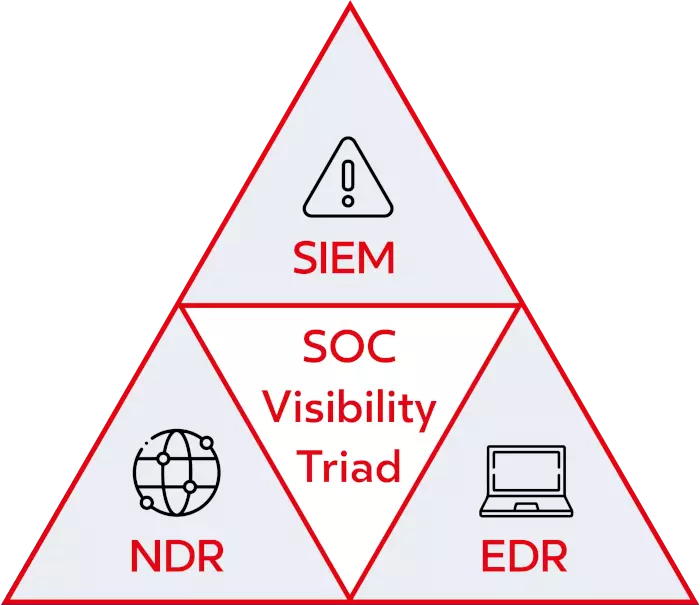
Transparency in every corner - that's what this security model developed by Gartner is all about: SIEM, NDR and EDR solutions reinforce each other and balance out weaknesses:
- SIEM relies on log file analysis to detect threats and vulnerabilities. The problem is that certain system exploits and vulnerabilities do not or rarely show up in the logs. In addition, certain technologies and systems do not allow or support log capture. Any SIEM is only as good as its data source.
- NDR complements the log analysis that a SIEM solution performs: Detected threats are correlated with network activity, closing (possible) logging gaps. NDR provides the important network data that the SIEM needs to give context to the various threats and vulnerabilities it detects.
- EDR is a predominantly behavioural security technology that focuses on detecting malicious activity that takes place directly on an endpoint (server, desktop, laptop). This makes it possible to detect the signs of an attack at the earliest possible stages and isolate the affected devices from the network at an early stage.
Gartner's security recommendation - meaningfully extended at dacoso
In the dacoso SOC, you benefit from the security pyramid defined by Gartner in the so-called "SOC Visibility Triad" - and you get even more: Managed SIEM, Managed NDR and Managed EDR are supplemented by Threat Hunting (Managed TIS) and explicit Vulnerability Management (Managed VAS) - for even better detection and defence against risks and attacks.