Managed NDR
Detect attacks
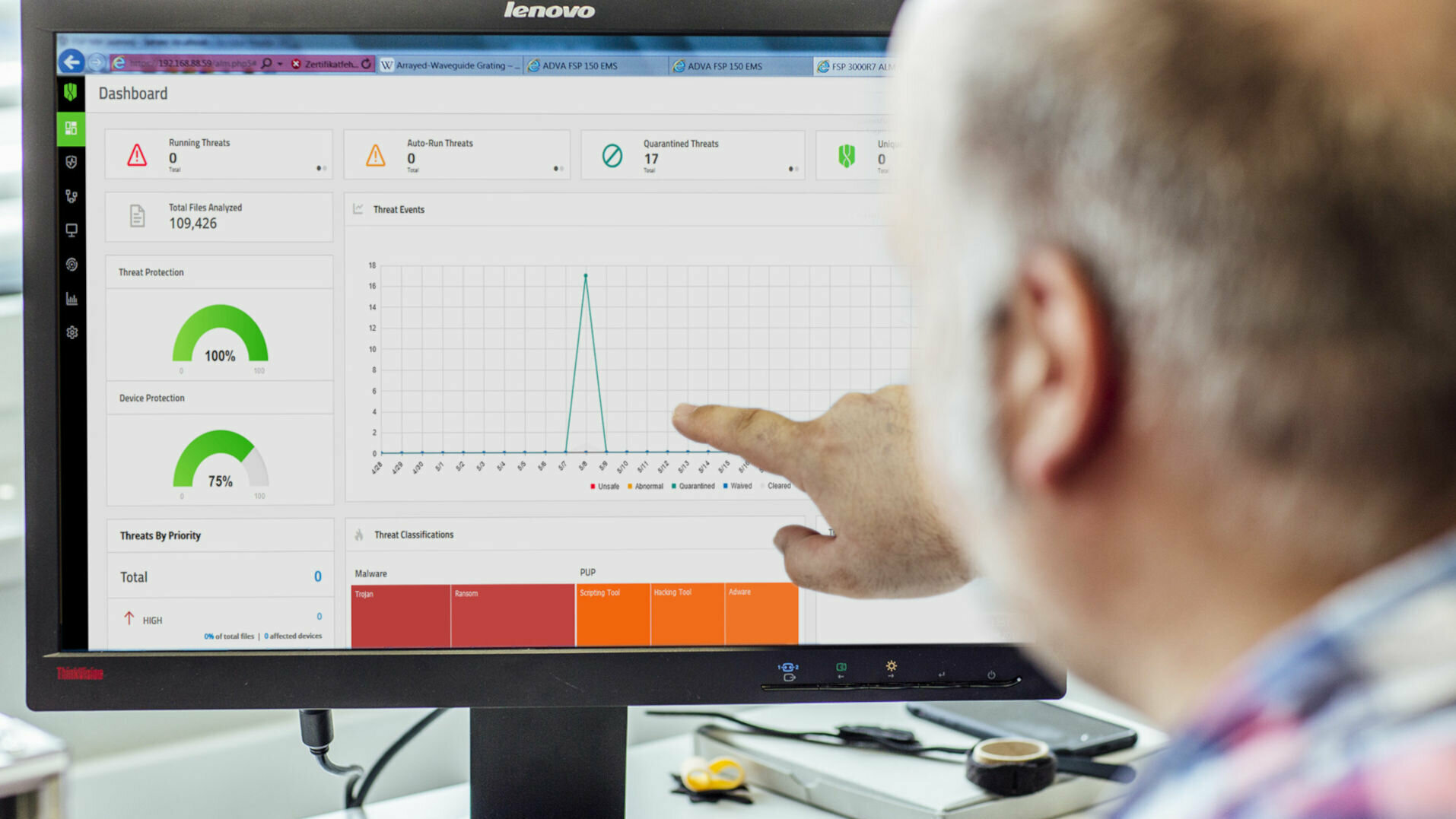
There is a lot going on in corporate networks - no wonder that cyber attacks often go undetected. It is not uncommon for several months to pass before security incidents are even detected. Defend yourself in good time and use Managed NDR (Network Detection & Response) for your network security: Network monitoring detects threats, initiates countermeasures on request and thus ensures more security by protecting your data from hackers and digital espionage.
For example:
- Attacks against user accounts, unauthorised attempts to access systems or even just tapping them for corresponding possibilities (lateral movement and information gathering).
- The attempt by an attacker, after a successful attack, e.g. via spear phishing or malware, to establish a return channel to his command & control server on the Internet or to another external system or service in order to exfiltrate data.
- Common attempts to access various network shares in the event of a ransomware outbreak
- Unusual connections that suddenly go out from certain systems, as may be the case after a supply chain attack, for example.
With the help of sensors in the network, NDR records all traffic data. This data serves as a valuable source for detecting anomalies. To do this, NDR solutions typically use a combination of techniques including machine learning, behavioural analysis, Indicators of Compromise (IoC) and retrospective analysis. NDR systems analyse both north/south and east/west traffic on the network. Other systems such as IDS/IPS and firewalls usually only monitor the network perimeter (network edge). In addition to monitoring the network, NDR also provides an initial, automated incident response to threats through certain response functions.
Managed NDR: Intelligent Network Monitoring
Our Managed NDR solution is based on a self-learning system using machine learning algorithms for your network security. After a learning phase, it detects unusual actions that deviate from the previous normal behaviour in the network. In this way, we also identify attacks for you that try to stay under the radar. If it is a critical security incident, we contact you immediately. Depending on the event, certain countermeasures - e.g. blocking a connection or isolating a system - can take effect automatically and thus extremely quickly. This allows attacks to be stopped at a very early stage, which is extremely important in the case of ransomware incidents, for example.
In addition, our security experts also use NDR for Advanced Threat Protection (ATP): Through continuous network monitoring, the history of even advanced and hidden attacks can be traced, where signature-based security tools can cut their teeth. Our solution uncovers the disguised communication channels based on deviations from normal data traffic and contributes specifically to advanced threat protection and threat hunting.
Side effect: optimise systems
He who observes notices a lot! Use our NDR solution for better security management in your network - for example, to identify unsafe and undesirable protocols and to verify technical specifications. In addition, almost any number of additional rules can be defined, and an alarm is triggered if they are not complied with. In regular reports, we recommend operational measures with which you can ensure even better protection in your network.
- Your networks are better protected: through automated detection of attack activities (unknown or known methods, targeted or untargeted attacks, ransomware, supply chain attacks, advanced persistent threats, exploitation of zero-days) and automatable countermeasures.
- Machine Learning perfects attack detection
- You use side effects for more security hygiene: detection of insecure protocols or undesired communication relationships
Monitored in the BSI-certified SOC
Together with you, we design an optimal NDR architecture. Based on this, we place sensors at suitable points in the network, at network transitions or in the cloud. These sensors send metadata extracted from the traffic to a central NDR component for analysis, which is also installed on-premise on your premises. We connect this NDR component to our BSI-certified Security Operations Centre (SOC) via a secure Virtual Private Network (VPN). From there, our security experts monitor the IT security of your corporate network, your OT environment and your cloud services around the clock. Security incidents are assessed for their relevance. And should there be a need for action, our experts provide well thought-out recommendations.
Are you interested in XDR?
XDR - this stands for Extended Detection & Response. If you want to comprehensively detect and block security incidents in your company, we offer you a combination of Managed NDR plus Managed EDR (Endpoint Detection & Response). This allows you to rely on the holistic detection of incidents in your entire network, including all end devices that are used in the company or in the home office: customised XDR for your exact requirements.